We have all been there. A missed decimal point, a late-night oversight, or a spreadsheet formula that somehow broke itself—human error is an inevitable part of being, well, human. But in the world of high-stakes finance, energy trading, or corporate treasury, a “simple” slip-up in limit compliance can cost millions in fines or cause a massive breach of risk appetite.
For years, we’ve relied on static systems and manual checks to keep us within bounds. But as the pace of business accelerates, “static” isn’t cutting it anymore. Enter Agentic AI.
What Makes “Agentic” AI Different?
Standard AI is like a high-end calculator: you give it data, and it gives you an answer. Agentic AI, however, is more like a digital colleague. It doesn’t just process data; it takes initiative.
In the context of limit compliance, an Agentic system doesn’t just wait for a breach to happen and then send a frantic email. It perceives the environment, understands the rules (the limits), and proactively maneuvers to ensure those rules are never broken in the first place.
From Reactive to Proactive: The Three Big Shifts
How exactly does this change the day-to-day for compliance teams? It boils down to three major shifts:
- Continuous Monitoring vs. Batch Checks: Instead of checking limits at the end of the day, Agentic AI monitors every transaction in real-time. It’s the difference between a smoke detector and a fire suppression system that’s always on.
- Contextual Understanding: Humans are great at understanding why a limit matters. Basic software isn’t. Agentic AI bridges this gap by analyzing market volatility and news cycles to understand if a “near-miss” is a one-time fluke or a sign of a larger systemic risk.
- Autonomous Course Correction: If a trader is approaching a concentration limit, the AI agent can suggest specific hedging strategies or alternative trades to stay compliant without stopping the flow of business.
Why This is a Win for Humans
It’s easy to worry that “autonomous” means “out of control,” but it’s actually the opposite. By letting Agentic AI handle the tedious, high-frequency monitoring:
- Compliance Officers can stop being “police officers” and start being “risk architects.”
- Operational Stress drops significantly because the “fat-finger” mistake is caught by the system before it ever hits the market.
- Audit Trails become bulletproof. The AI documents every decision and every “nudge” it provides, making the next audit a breeze.
Meet ECLMS: Your Enterprise Partner in Intelligent Compliance
Moving “Beyond Human Error” requires more than just a philosophy—it requires the right architecture. This is where ECLMS (Enterprise Collateral and Limit Management System) steps in.
ECLMS isn’t just a database for your limits; it’s a centralized “Command Center” designed to eliminate silos and automate the high-stakes world of collateral and risk.
Features Built for the Modern Compliance Era: ECLMS
- To bridge the gap between human error and regulatory excellence, we’ve developed ECLMS (Enterprise Collateral and Limit Management System). Designed specifically for the Indian financial landscape, ECLMS doesn’t just manage data—it masters compliance.
Here is how ECLMS transforms your risk management:
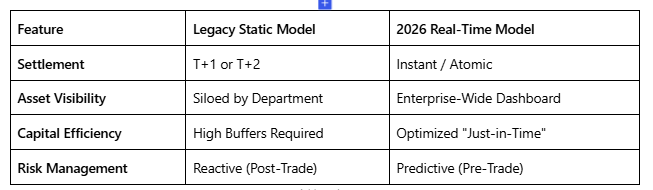
- Real-Time Limit Orchestration: No more “post-facto” alerts. ECLMS monitors multi-currency and multi-entity limits—including Large Exposure Framework (LEF) and Group-wide investment limits—at the exact moment of execution.
- Dynamic Collateral Optimization: Automated LTV (Loan-to-Value) tracking and real-time revaluation for a variety of asset classes (Gold, Shares, Real Estate). It ensures you never fall short of RBI’s haircut requirements during market volatility.
- Automated Regulatory Guardrails: Built-in logic for the latest RBI Master Directions (2025-26), including transaction-level materiality thresholds for Related-Party Lending and concentration caps for NBFCs and HFCs.
- Intelligent “What-If” Simulations: Before committing to a large exposure, run “What-If” scenarios to see the immediate impact on your Tier I capital, risk-weighted assets, and headroom.
- Immutable Audit Trails: A tamper-proof, time-stamped log of every limit change, breach, and override. When the RBI auditors arrive, your “Compliance Health Report” is ready in one click.
Limit compliance shouldn’t be a game of “catch me if you can.” By using Agentic AI, firms are moving past the limitations of human fatigue and outdated software toward a future where compliance is seamless, invisible, and ironclad.
Don’t wait for a penalty to realize your system is outdated.
Move beyond human error and into a state of “Compliant by Design.”